Introduction

Date created: May 7, 2019
Last updated: May 7, 2019
Today I received an email titled “jhanley@www2.jhanley.com has been hacked, change your password ASAP”. The hacker claims to know my login and password, has full control over my account and has sent this email using my credentials.
I doubt that the email is legitimate, but I want to be certain. This email gave me the idea to write this article so you know how too.
I use Mailbird for my email accounts (and Outlook also). Mailbird does not give me any warnings about this email. I like Mailbird because of the feature to combine multiple email accounts (identities) into one view.
Below is a screenshot showing this email in Mailbird. I am including a screenshot instead of the actual email for everyone’s safety.
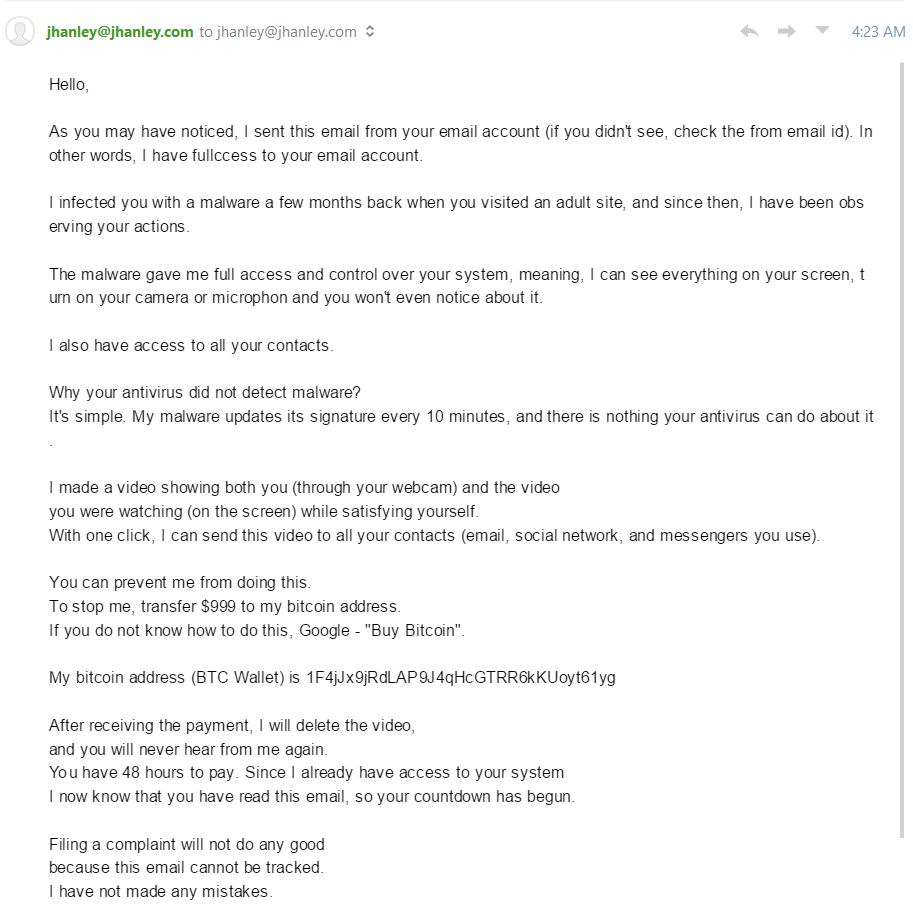
A warning sign is spelling errors for critical words or phrases important to the sender’s message. Examples: fullccess and microphon
I fired up Chrome and logged into Gmail. Gmail showed a big red warning.

Thank you G Suite/Gmail, this warning is appreciated.
I use G Suite for the jhanley.com domain. I also have SPF, DKIM and DMARC enabled. This makes the job for a spammer much harder. However, I want to be certain that my credentials were not used to send this email.
One item I have noticed about G Suite is that when I send myself an email using the same G Suite organization, the email does not contain a lot of headers that are common when email traverses external email servers.
Let’s compose an email, send it to ourselves, and analyze the email headers.
Open the email in Gmail and click the three vertical dots menu at the right-hand side of the email and select “show original”.
Gmail will now display the raw text version of the email.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
MIME-Version: 1.0 Date: Tue, 7 May 2019 20:41:21 -0700 Message-ID: <CAObL8FatEYQJPvan25uU1+y6Q-Y-XX-4PhjKQ5+iyzpbFPthGw@mail.gmail.com> Subject: Test Email to Analyze Headers From: John Hanley <test@jhanley.dev> To: John Hanley <test@jhanley.dev> Content-Type: multipart/alternative; boundary="0000000000001687990588581bc5" --0000000000001687990588581bc5 Content-Type: text/plain; charset="UTF-8" Small email message body for testing purposes. --0000000000001687990588581bc5 Content-Type: text/html; charset="UTF-8" Content-Transfer-Encoding: quoted-printable <div dir=3D"ltr"><span style=3D"font-family:Arial,sans-serif;font-size:9pt"= ></span><span style=3D"display:inline-block;height:23px"><span>Small email = message body for testing=C2=A0purposes.=C2=A0=C2=A0</span></span><br></div> --0000000000001687990588581bc5-- |
The part we are interested in begins with MIME-Version: 1.0 and continues to Content-Type: text/plain; charset="UTF-8". Everything in between is the Email headers. Notice that there is no mention of any exchanges between external servers. This means that G Suite internally managed this email. The email went from my account to my account without going out onto the Internet.
Now let’s look at the email headers for the ransom email:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 |
Delivered-To: test@www2.jhanley.com Received: by 2002:a92:9e8f:0:0:0:0:0 with SMTP id s15csp3750510ilk; Tue, 7 May 2019 04:23:09 -0700 (PDT) X-Google-Smtp-Source: APXvYqyGMWEupu2ZRKVBvvZfcoo4LlPkOHPyX83Irzcy7IfSf2Pev8HznnU3L0d5e1cowbhNE9Gk X-Received: by 2002:ab0:130b:: with SMTP id g11mr3119321uae.74.1557228189551; Tue, 07 May 2019 04:23:09 -0700 (PDT) ARC-Seal: i=1; a=rsa-sha256; t=1557228189; cv=none; d=google.com; s=arc-20160816; b=cH/VM8k1SXmE9UqfN8hG3g1cPl5RgXAUEmsuDthnjPZO7Ju6302OJ/O4GCGlYK0kOc izqAu2whBqTWUq2tyqe7JJxpc/vOGKikBy77cXamUsskuYOdT+8AkQvvlXJVv/018Eqe 99uA8jTn72ADDv3cAozglcobOrMFhthSe+3aRlij4TR0XG2PpoBr04LCskJdlKBXZPMs 3urnUFU/hThJaPNr04w0FJ8F11PJKLwcqu5u2harMgPAiD7pLv3dkYFaYP5nktpjaZwI XZtg5bnt/uVnjWDzRqMp7q3Wybw5pRtQxOS61Xd2UG4meGa55eoiIra8peJNNag4s+Rb g98g== ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816; h=content-transfer-encoding:subject:to:mime-version:user-agent:from :reply-to:date:message-id; bh=WCcyZOO9Hrl6J7bMKG28d5nCwrgum9Z0AefuQDP2Th0=; b=HaAnUA7o5yayRyjk9Tb/MClghGWbaa6y9z7zVcMzrc2jbGC6MKVFmrku0pkw+PoTs6 kaJxlDsJqxiH6CE4nup5efMubLgSEqfhczy7stBv+wn9Zexx5LoFycORh2B597NP5C9k pOvqwmq4z/ovQRQqmzPYrkvJpD3/geFfN6GJiTaoGe2gxlo14I49FyU2Z3yA+pK783fX 0kM4yyQlunJp57G1CF8eUT1bCYaWe3rnNtnDy3O1Y03SuXOGGOhCysR5+EcZ6UR3qZaK yUS+sY2CtK+/YuWGDCWu+bgAqnD8VS9F1PmsEspbytWmBqtrpWesbAbBHcwUCbcQZxUt a1yg== ARC-Authentication-Results: i=1; mx.google.com; spf=neutral (google.com: 203.153.42.190 is neither permitted nor denied by best guess record for domain of koweaoj@xaae.com) smtp.mailfrom=koweaoj@xaae.com; dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=jhanley.com Return-Path: <koweaoj@xaae.com> Received: from xaae.com ([203.153.42.190]) by mx.google.com with SMTP id r10si2246245vsc.434.2019.05.07.04.23.02 for <test@www2.jhanley.com>; Tue, 07 May 2019 04:23:09 -0700 (PDT) Received-SPF: neutral (google.com: 203.153.42.190 is neither permitted nor denied by best guess record for domain of koweaoj@xaae.com) client-ip=203.153.42.190; Authentication-Results: mx.google.com; spf=neutral (google.com: 203.153.42.190 is neither permitted nor denied by best guess record for domain of koweaoj@xaae.com) smtp.mailfrom=koweaoj@xaae.com; dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=jhanley.com Received: from unknown (83.25.105.125) by mx03.listsystemsf.net with ESMTP; Tue, 07 May 2019 07:20:08 -0400 Received: from qnx.mdrost.com ([25.85.71.11]) by webmail.halftomorrow.com with SMTP; Tue, 07 May 2019 07:07:17 -0400 Received: from [138.177.36.230] by asx121.turbo-inline.com with SMTP; Tue, 07 May 2019 07:05:37 -0400 Message-ID: <7BC6E284.EF495FCF@xaae.com> Date: Tue, 07 May 2019 07:05:37 -0400 Reply-To: test@www2.jhanley.com From: jhanley@www2.jhanley.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.0; de; rv:1.8.1.18) Gecko/20081105 Thunderbird/2.0.0.18 MIME-Version: 1.0 To: <test@www2.jhanley.com> Subject: jhanley@www2.jhanley.com has been hacked, change your password ASAP Content-Type: text/html; charset="us-ascii" Content-Transfer-Encoding: base64 DQoNCkgmIzgyMDM7ZTwhLS0gamhhbmxleSAtLT5sJiM4MjAzO2w8IS0tIGpoYW5sZXkgLS0+byYj |
I have truncated the email as the email body is large and is not important to this article.
If you look at the last line, which is the start of the email body, notice that this looks different from normal readable text. Look at the third line from the bottom: Content-Transfer-Encoding: base64. The spammer is trying to get past spam detectors. There is nothing wrong with encoding an email base64, but this is something to notice. All professional software will just decode the base64 text and process as usual.
I did take the time to decode the base64. This spammer tried to double hide their email body by filling the body with lines like this:
<!-- jhanley -->s​e<!-- jhanley -->
The email body comprises lots of comments, plus they encode every character. Again, professional software can handle this with no problem. Remember, in order for you to read their ransom demand, an email client must be able to decode this, therefore other well-written software can too.
As you scroll thru each header line, you can see the exchanges that occurred over the Internet. There is some activity that includes IP addresses. Now I am confident that this email originated outside of G Suite/Gmail and they did not use my account credentials to send this email.
Let’s analyze further to see if there are any more concerns.
Look for this line:
Return-Path: <koweaoj@xaae.com>
The header Return-Path is what an email server checks when verifying SPF. The spammer is not smart. To make this email look like it came from me (as stated in his email), then the Return-Path should be inside my domain.
Look for this line:
spf=neutral (google.com: 203.153.42.190 is neither permitted nor denied by best guess record for domain of koweaoj@xaae.com)
The domain xaae.com does not have an SPF record. Therefore Google cannot determine the SPF policy.
My domain has an SPF record of v=spf1 include:_spf.google.com ~all. The ~all means soft fail. If instead, the SPF record is v=spf1 include:_spf.google.com -all, the error would be Hard Fail. From this, we also now know that the sender is not inside my domain. The sender (which can be forged) is koweaoj@xaae.com. The spammer is not too bright …
I did look up xaae.com and it is a real domain registered to someone in Panama City, Panama. Do not place too much importance on this information. The validity depends on the email servers between the spammer and Google.
Look for this line:
dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=jhanley.com
Excellent, now our DMARC policy is kicking in and saying there is a problem with this email. I have my DMARC settings as v=DMARC1; p=none; rua=mailto:nvusw1e5@ag.dmarcian.com;. The p=none means detect problems but do not reject email. I should receive an email report at dmarcian.com to review. Most companies will want to use p=quarantine or p=reject.
Manage suspicious emails with DMARC
My domain also has DKIM enabled. I won’t go into details here about DKIM, but the spammer has no way of digitally signing this email, so this is another indicator that this email is bogus – the email is missing my domain’s DKIM signature.
In summary, this email demanded that I send bitcoins to his account. The spammer stated that he used my computer to record a video of me – oops; I don’t have a video camera attached to my computer. The email headers clearly indicate that this email was not sent using my G Suite/Gmail credentials.
It is safe to ignore this spammer and delete the email.
This email is a good example of why you want to set up SPF, DKIM, and DMARC for your domain. You do not want a spammer sending ransom emails using email addresses that look like you. You do not want spammers sending you, your employees, or your contacts harmful or inappropriate emails. Time is money. Let’s make a spammer’s job difficult, expensive and pointless.

I design software for enterprise-class systems and data centers. My background is 30+ years in storage (SCSI, FC, iSCSI, disk arrays, imaging) virtualization. 20+ years in identity, security, and forensics.
For the past 14+ years, I have been working in the cloud (AWS, Azure, Google, Alibaba, IBM, Oracle) designing hybrid and multi-cloud software solutions. I am an MVP/GDE with several.
Leave a Reply